The first, we need to know what, why we use docker registry.
What is a Docker Registry?
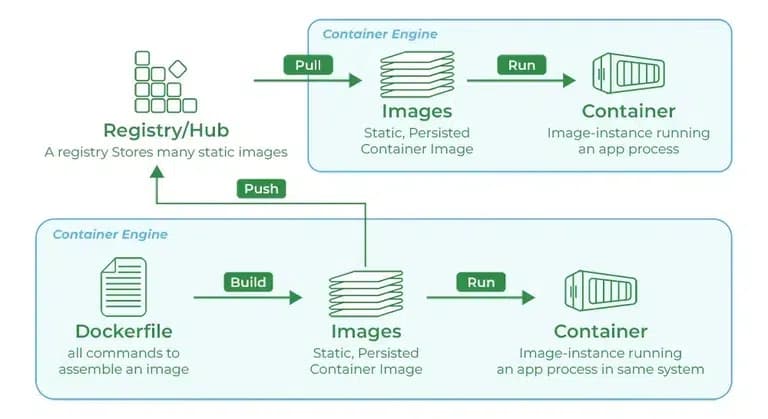
A Docker registry is a service that stores and distributes Docker images. It is an essential component in the Docker ecosystem, providing a centralized location to manage and share container images.
Is is a storage and content delivery system that holds named Docker images, available in different tagged versions. Users can push images to the registry and pull images from the registry.
Why Use a Docker Registry?
1.Centralized Image Management:
A Docker registry provides a centralized location to store and manage Docker images. This makes it easier to organize, version, and share images across different environments and teams.
2.Efficient Image Distribution:
Docker registries enable efficient distribution of Docker images. Instead of manually transferring images between systems, you can push images to the registry and pull them from any location with network access.
3.Version Control:
Docker registries support versioning of images through tags. This allows you to maintain multiple versions of an image, making it easier to roll back to previous versions if needed.
4.Collaboration
A Docker registry facilitates collaboration among development teams. Team members can push their images to the registry and share them with others, ensuring consistency and reproducibility across different environments.
5.Deployment Automation
Docker registries are often integrated into CI/CD pipelines. This allows for automated building, testing, and deployment of Docker images, streamlining the development and deployment process.
6.Security
Using a private Docker registry allows you to control access to your images. You can implement authentication and authorization mechanisms to ensure that only authorized users can push or pull images.
Benefits of Using a Docker Registry:
• Centralized Storage: Keeps Docker images in one place, making them easy to find and manage.
• Efficient Sharing: Simplifies sharing images between teams or environments without manual file transfers.
• Version Management: Tracks different image versions using tags for easy updates or rollbacks.
• Collaboration: Enables teams to work together seamlessly by accessing shared images in the registry.
• CI/CD Integration: Automates image building, testing, and deployment in development pipelines.
• Enhanced Security: Restricts image access with authentication and authorization controls.
Simple Example:
Imagine a software team developing a web app.
1.Without a Docker Registry:
Each developer has to manually share their Docker images via email or external drives, leading to confusion about which version is the latest and wasting time.
2.With a Docker Registry:
• Developer A builds a new app image and tags it webapp:v2.0.
• They push the image to the registry.
• Developer B pulls webapp:v2.0 from the registry and runs it without needing extra steps.
• Later, the CI/CD pipeline automatically deploys webapp:v2.0 to production, ensuring everyone uses the same version.
This streamlines collaboration, ensures consistency, and integrates smoothly with deployment workflows.
Hope that your guys have some info about docker registry so how to use docker registry?
Here are some popular Docker registries, both public and private, that you can use to store and manage your Docker image
Docker Hub
GitHub Container Registry
Google Container Registry (GCR)
Amazon Elastic Container Registry (ECR)
Azure Container Registry (ACR)
Each Docker registry has its own set of limits and considerations and special those have fee. The docker hub do have limit but we need to public the image but there are situations where you will not want your image to be publicly available. Images typically contain all the code necessary to run an application, so using a private registry is preferable when using proprietary software. This is reason I written this blogs.
In this tutorial, you will set up and secure your own private Docker Registry. You will use docker compose to define configurations to run your Docker containers and Nginx to forward server traffic from the internet to the running Docker container. Once we completed this tutorial, we will be able to push a custom Docker image to owner private registry and pull the image securely from a remote server.
What stuff do we need to have:
In the server, create folder to setup docker compose for docker registry
Create and open a file called docker-compose.yml by running:
Add config for ~/docker-registry/docker-compose.yml, which define a basic instance of a Docker Registry:
Run docker compose
Output:
Verify the Registry is Running:
You can verify that the registry is running by accessing it in your web browser or using
or on check directly on server
Output logs:
Setup basic authentication:
Install apache2-utils
Create the .htpasswd file and add a user - admin
Config password
You will be prompted to enter and confirm a password - confirm password for the user admin.
Check config account after run cli above:
Output
Note: Setting up basic authentication for your Docker registry is important to secure access to your registry. Without authentication, anyone who knows the address of your registry can push or pull images, which can lead to unauthorized access and potential security risks
Configure Nginx:
Edit your Nginx configuration file (e.g., /etc/nginx/sites-available/default) to include the following configuration
Restart Nginx to apply the changes:
Now you can verify the Registry is Running:
Response should be returned {}
Public image
Now that your Docker Registry server is up and running, and accepting large file sizes, you can try pushing an image to it. Since you don’t have any images readily available, you’ll use the ubuntu image from Docker Hub, a public Docker Registry, to test.
From server create test image
Check the image
The new image is now available locally, and you’ll push it to your new container registry. First, you have to log in:
In my case, I use ~ docker login https://registry.astalife.co. Then enter user name and password that we configured above
Once we’re logged in, tag the created image:
Finally, push the newly tagged image to your registry:
Output:
Open https://registry.astalife.co/v2/_catalog to check iamge pushed
Output:
Pull image from private registry from client:
Now that we’ve pushed an image to your private registry, we can pull from it.
On the client, log in with the username and password you set up previously:
Pulling the test-image by running:
Check docker image
Now you can use this image from the client to.
Conclusion
In this post we set up our own private Docker Registry, and published a Docker image to it. By Docker containers in your workflow, you can ensure that the image containing the code will result in the same behavior on any machine, whether in production or in development and avoid some limit such as Bandwidth, Storage.
Get more code setup: https://github.com/AstaDK/private-docker-registry/tree/feat/private-registry-ss1